Impossible, so we offer Cyber Security ensuring your data protection from any external threat.
Managing business on the digital front is not easy when there are security threats and penetrative attacks that can harm your business and brand reputation. It is essential to opt for cyber security that will ensure all is managed well.
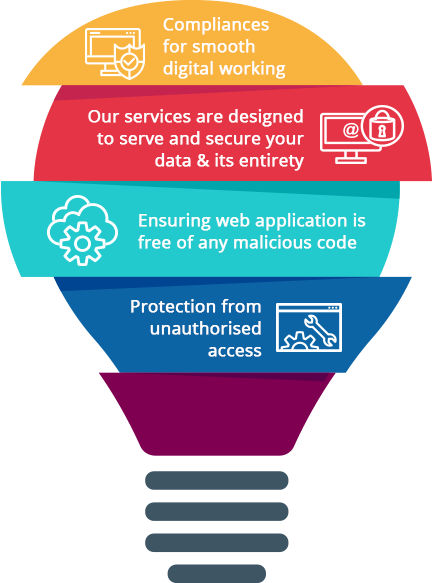
We offer our custom made cyber security solutions that are designed to benefit you by providing protection against cyber-attacks, proactively analyzing and providing robust firewall, security solutions designed to reduce cyber threats ensuring that your business information and data are handled and managed in a secured vault.
Training your staff to equip them against threat identification/handling and reporting, securing your system through robust security solutions and ensuring that your employees receive all the information/ training with regard to security awareness for managing cyber security on a 360 degree level covering all the essential aspects.

Security awareness training
Needless to say, protecting your system against various threats begin with security awareness, it is only through the proper channels that you and your employees receive security awareness training. Our offerings with security awareness training includes recognizing threats, avoiding threats, awareness of ransomware, viruses, robust password setting, browser security, recognizing/ avoiding phishing attacks and safekeeping and protecting removable media.












