AWS Amazon GuardDuty is a threat detection service provided by AWS cloud that analyzes various logs and events and identifies unauthorized and malicious activities in our AWS environment. The data sources from which GuardDuty extracts information are:
- AWS CloudTrail event logs
- AWS CloudTrail management events
- AWS CloudTrail data events for s3
- Kubernetes audit logs
- VPC flow logs
- DNS logs
Steps to enable AWS Amazon GuardDuty:
- Login to your AWS cloud account and then go to the GuardDuty console.
- After that click on Get Started.
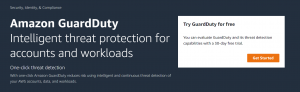
- Click on Enable GuardDuty.
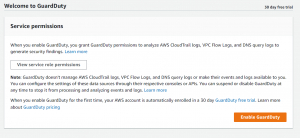
- GuardDuty is now enabled.
Finding: These are the potential security threats identified by GuardDuty. These can be seen in the console with detailed information about the threat.
Finding types by resources:
- EC2 finding types
- IAM finding types
- S3 finding types
- Kubernetes finding types
Suppression Rule: A suppression rule is a set of criteria consisting of a filter attribute and a value that is used to filter discoveries by automatically archiving fresh findings that meet the requirements. Suppression rules can be used to filter threats that you don’t intend to act on, making it easier to identify the security threats that have the most impact on your environment.
To add a suppression rule follow these steps:
- Go to the Findings page and then click on Suppress findings.
- After that Select filter criteria.
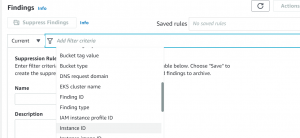
- Give a value for criteria. For example, if the selected criteria is Instance Id, then write the instance id and Apply.
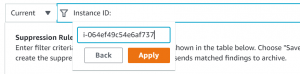
- Give name and description and then click on Save.
Export Findings: GuardDuty automatically exports findings to CloudWatch Events within 5 minutes after the finding is generated. We can configure it to export active findings to the S3 bucket.
Steps to export findings to s3 bucket:
- Go to Settings->Findings export options.
- Next, Click on configure now.
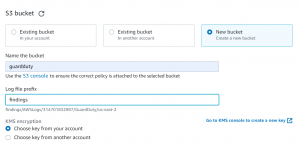
- Either select an existing bucket or create a new one.
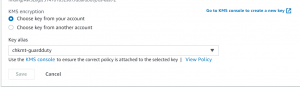
- AWS encrypts finding data with KMS key. We will create a KMS create, so click on the link for the KMS console.
- Click on create a key.
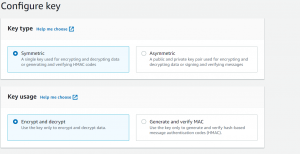
- Create an alias and click on Next.
- Select GuardDuty service and your user account as key administrator and give key usage permission to service and user.
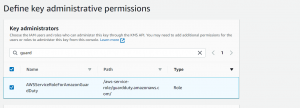
- Review the key policy and click on finish.
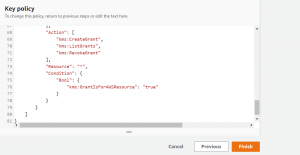
- Now in the GuardDuty console select the KMS key and click on Save.
How to configure the AWS CloudWatch Events rule to notify you of Amazon GuardDuty findings:
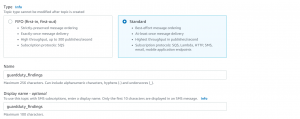
- First, we need to create an SNS topic. For that go to the SNS console and click on Create topic.
- Select Standard type and give name and description and then click on Create topic.
- Go to Subscriptions->Create Subscription.
- Select your Topic ARN and protocol. We will be using email.
- Click on Create subscription.
- Go to your email and confirm the subscription.
- Now go to the Amazon Eventbridge console and click on Create Rule.
- Enter the name for your rule and click next.
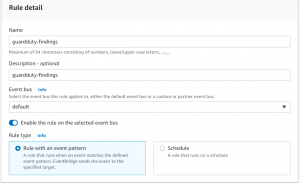
- Select AWS events as event source,
- In Event Pattern select GuardDuty as AWS service and GuardDuty Finding as the Event type.
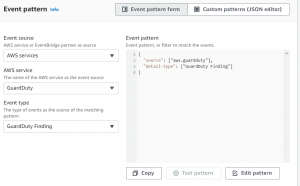
- Click on Edit pattern and paste the following code there.
{
"source": [
"aws.guardduty"
],
"detail-type": [
"GuardDuty Finding"
],
"detail": {
"severity": [
4,
4.0,
4.1,
4.2,
4.3,
4.4,
4.5,
4.6,
4.7,
4.8,
4.9,
5,
5.0,
5.1,
5.2,
5.3,
5.4,
5.5,
5.6,
5.7,
5.8,
5.9,
6,
6.0,
6.1,
6.2,
6.3,
6.4,
6.5,
6.6,
6.7,
6.8,
6.9,
7,
7.0,
7.1,
7.2,
7.3,
7.4,
7.5,
7.6,
7.7,
7.8,
7.9,
8,
8.0,
8.1,
8.2,
8.3,
8.4,
8.5,
8.6,
8.7,
8.8,
8.9
]
}
}
- Select the SNS topic as the target and topic that we created.
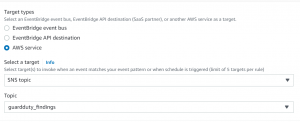
- Now go to additional settings and select Input transformer in configure target input.
- Copy the following code in the Input field.
{
"severity": "$.detail.severity",
"Account_ID": "$.detail.accountId",
"Finding_ID": "$.detail.id",
"Finding_Type": "$.detail.type",
"region": "$.region",
"Finding_description": "$.detail.description"
}
- Copy the following code in Input template field.
"AWS <Account_ID> has a severity <severity> GuardDuty finding type <Finding_Type> in the <region> region." "Finding Description:" "<Finding_description>. " "For more details open the GuardDuty console at https://console.aws.amazon.com/guardduty/home?region=<region>#/findings?search=id=<Finding_ID>"
- Click confirm and next.
- Create tags.
- Review and click on create rule.
Please contact Checkmate Global Technologies cloud consultants to learn more about Infrastructure monitoring and Observability. You can also hire DevOps engineer to transform entire infrastructure monitoring stack.


