Identity Access Management
IAM is a service in AWS for security, it enables you to manage access to AWS services and resources in a very secure manner, with IAM you can create users and groups and you can allow these users to access a resource or deny them from doing something ………. Wait a person with litter or more experience with AWS services knows this but How to enable access for a user on a specific date and time? , it can be done just by adding a condition to the policy that you are using to give permission/access for creating a user/role, In this blog let’s learn how to create a custom IAM policy which allows the permission at a specified time period and attach it to a user.
below is the json syntax of a IAM policy which enables full access to all AWS services and resources.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "*",
"Resource": "*"
}
]
}
you can make the above policy to be enabled on a specific date and time by just adding some conditions to it, below given syntax is an example of a condition, and a Policy created with below given conditions enables permissions from 1AM on 22-aug/2022 to 06PM on 22-aug/2022,
"Condition": {
"DateGreaterThan": {
"aws:CurrentTime": "2022-08-22T01:00:00Z"
},
"DateLessThan": {
"aws:CurrentTime": "2022-08-22T18:00:00Z"
}
}
below given Json syntax is of a policy which gives full administrative access on all the AWS resources in a specific date and time.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "*",
"Resource": "*",
"Condition": {
"DateGreaterThan": {
"aws:CurrentTime": "2022-08-22T00:00:00Z"
},
"DateLessThan": {
"aws:CurrentTime": "2022-08-22T07:10:00Z"
}
}
}
]
}
Creating a Customer Managed IAM Policy
To create custom/ user managed IAM policy login to your AWS web console and go to Policies under AWS Access Management in IAM and click on create policy

In step:1 click on JSON and give your syntax here and click on Next to gives tags to your policy in step:2.

And in step:3 give a name and description(optional) to your policy , review the details and click on Create Policy.

Once the policy is created you can see it in your policies list and now you can use it to create users and roles.
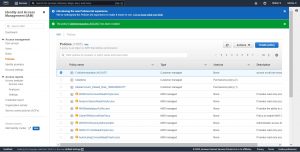
Creating New IAM user From AWS Web Console
Now Let’s create a new user with the custom policy we have created in last step, go to users under Access Management in IAM and click on Add users .

Next in step-1 give username and select access type based on your requirement and click on next to give permissions to the user.
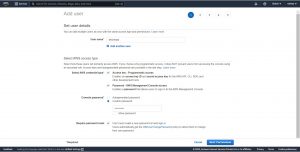
then in step-2 click on Attach existing policies directly and select the policy that you have created, you can use Filter policy to select customer managed policies and click on next to gives tags to your user .
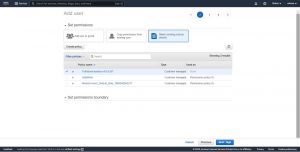
In step:4 review all the details and click on create user
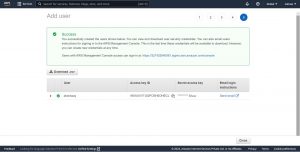
Then finally in step 5 download the access credentials or copy Access key ID and Secret Access key to provide them to the user intended to use them.
In this blog we have seen how to restrict a user to access the resources in a particular date and by creating a customer managed IAM policy.
Please contact our technical consultants if you have anything to be discussed related to cloud infrastructure .


